shift change 2024-02-27
Welcome to your shift change report: news (with a pinch of zesty analysis) from the off-going watch to the oncoming on anything interesting in privacy, security, or intelligence.

Over the past week security media, personalities (yeah, influencers), and marketing departments have gone into overdrive to hype the “takedown” of LockBit. Pats on the back and cheers all around, heck, the cops even got some credit for “trolling” the ransomware community after The Great Takedown (this is—should be—cringe-y stuff for professionals).
The only problem was that it was all bullshit. A takedown of sites and resources certainly did happen, but then the conclusions drawn from those specific facts (certain servers, certain sites, certain people, certain wallets, not The Organization) was that, in the words of The National Crime Agency “the NCA has taken control of LockBit’s services, compromising their entire criminal enterprise.”
And a week later LockBit is back up and running.
This was so utterly predictable I gave it a “Sure, Jan” for reliability the day it was announced. Why was I so confident? I’ll recap my post from last week about the sheer amount of money these groups make:
The purpose of the conspiracy, make money.

The effect of the conspiracy, they made a ton of money.
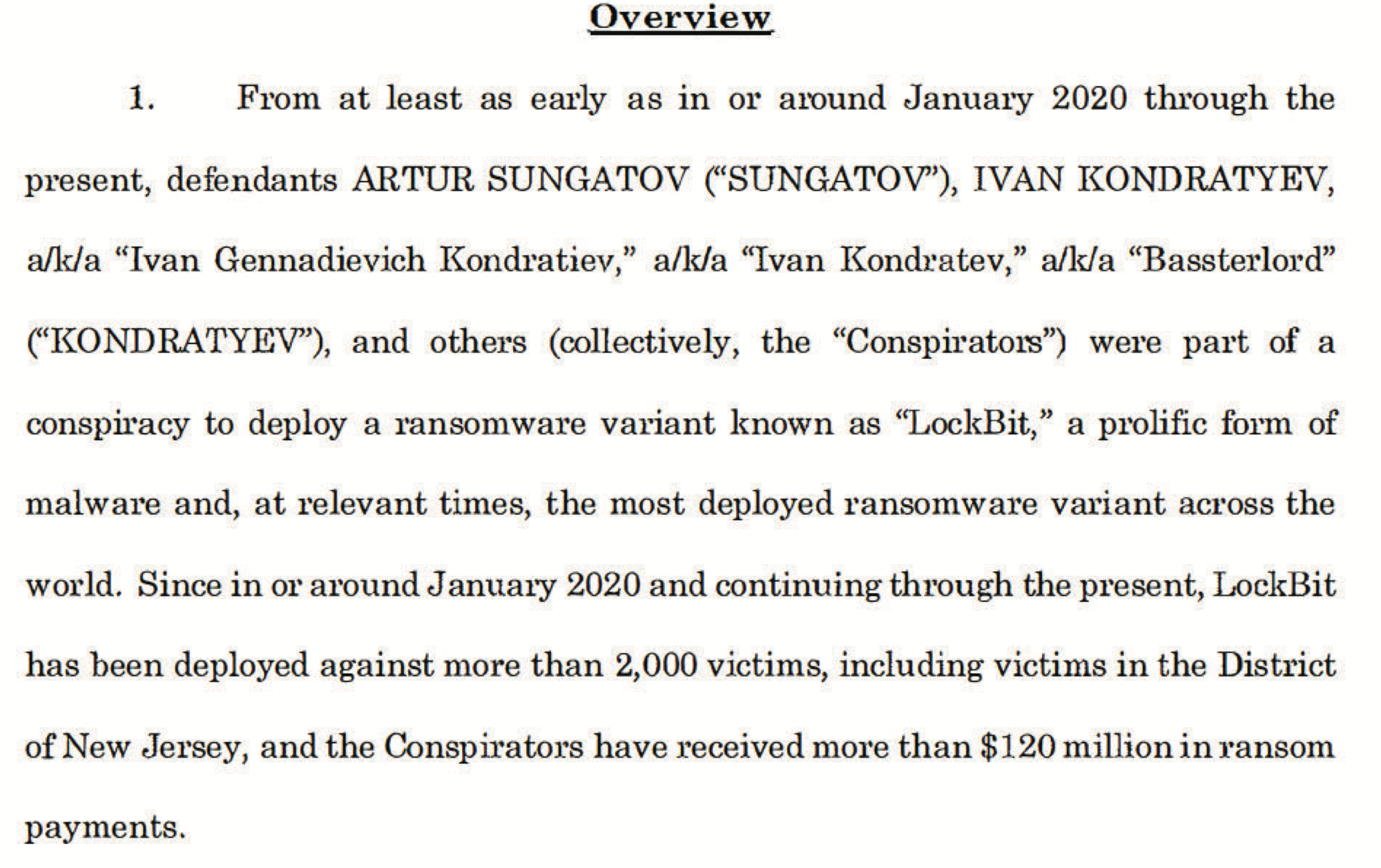
Incentives matter, and right now “a” takedown is not dealing 120 million in damage, until the math changes LockBit will always return in some form.
If you need further indication the takedown did not have the impact the cop-trolls want you to believe, Fulton County still does not control its own court records. Good trolling.
2. NIST releases CSF 2.0; recruiters and hiring managers release job descriptions that want 3-5 years of experience on the new framework.

Here is the CSF, direct.
Key takeaways for the new framework:
- Any and all organizations can use the framework, it is not targeted to critical infrastructure because the risks are no longer limited or likely to be limited to only critical infrastructure. Awesome!
- There are a ton of resources, tools, and help available. If you believe your security program has nothing to go on, or nothing to start with—start here.
3. North Korea v. Russia, espionage amongst quasi-aligned parties of mutual interest.

Allies spy on each other. That’s the story:
Spying on one's friends may be uncouth, but "it is not uncommon for intelligence agencies to spy even on their putative allies, if for nothing else, for insights to either strengthen the relationship or to identify and mitigate threats to the relationship," [John] Bambenek [of Bambenek Consulting] points out.
If this is surprise news to you, take a look at Israel spying on the US, or the US spying on errrrrybody.
## The shift change is a collection of timely stories of interest in the security, privacy, and intelligence worlds. Thanks for reading, and feel free to reach out to will@signaltonoise.fyi for any questions, comments, or thoughts on items you’d like to see highlighted (especially if it’s free, virtual, or networking that could help the community as a whole).