shift change 2024-02-21
Welcome to your shift change report: news (with a pinch of zesty analysis) from the off-going watch to the oncoming on anything interesting in privacy, security, or intelligence.
1. Signal lets you hide your phone number behind a screen name—this has been a long time coming.
Set a username, stop sharing your phone number—Signal has improved its base design privacy protections and we should all be here for it.
What do usernames provide:
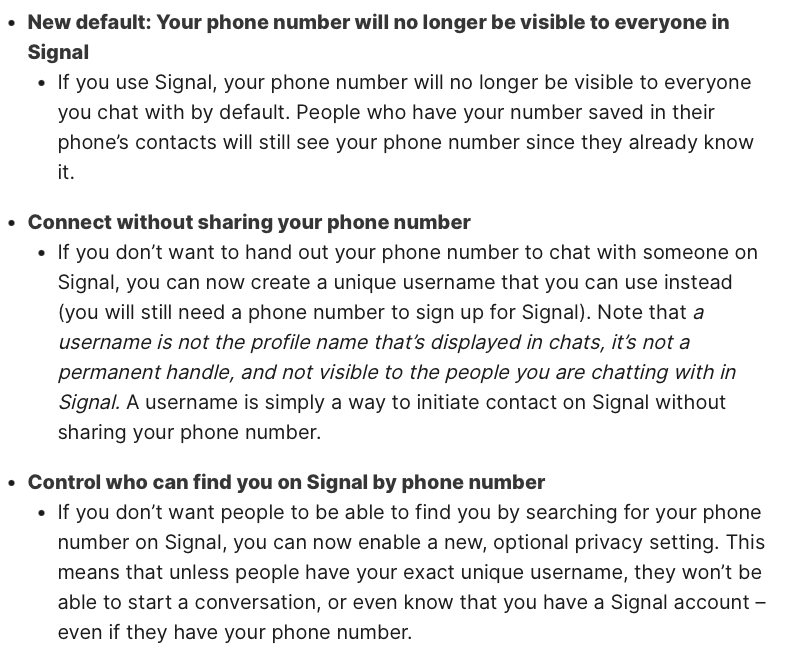
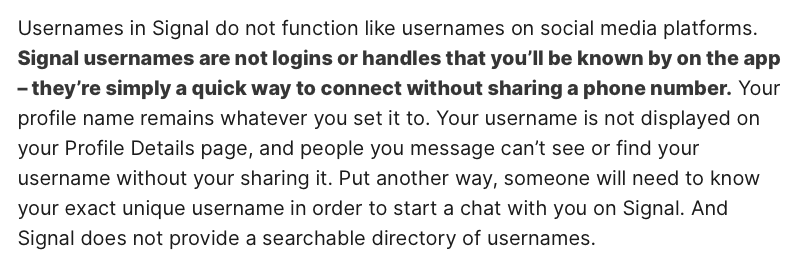
What usernames not provide:
2. Mandiant releases a maturity model for your intelligence program—how immature are you, really?

The model assesses capability across six domains:
- The organizational role of CTI
- Intelligence Services and CTI-use cases
- Analyst Capability and Expertise
- Intelligence Processes Lifecycle
- Analytic Practices and Products
- Tech Integration
I read this as “how well does your organization understand and use the intelligence cycle” with more detailed analysis and I love it. Cycle away.
You can get free assessments (depending on your self-awareness, and honesty) from Google Cloud’s Solution Center with a Workspace account (no generic Gmail allowed in these hallowed grounds).
3. Let’s look at those two LockBit indictments.

I am enthused by the international coordination and action frustrating LockBit’s ransomware endeavors. I just do not believe that a couple of indictments, and a dozen seized servers will have long term impact because the market incentives still available for ransomware service providers are still galactically beyond these punishments. In other words, ransomware service providers, whether they use the name LockBit or come back as LockBit 3000, aren’t going anywhere. How do I know that?
The goal of the conspiracy is/was to make money:

And they made a lot:
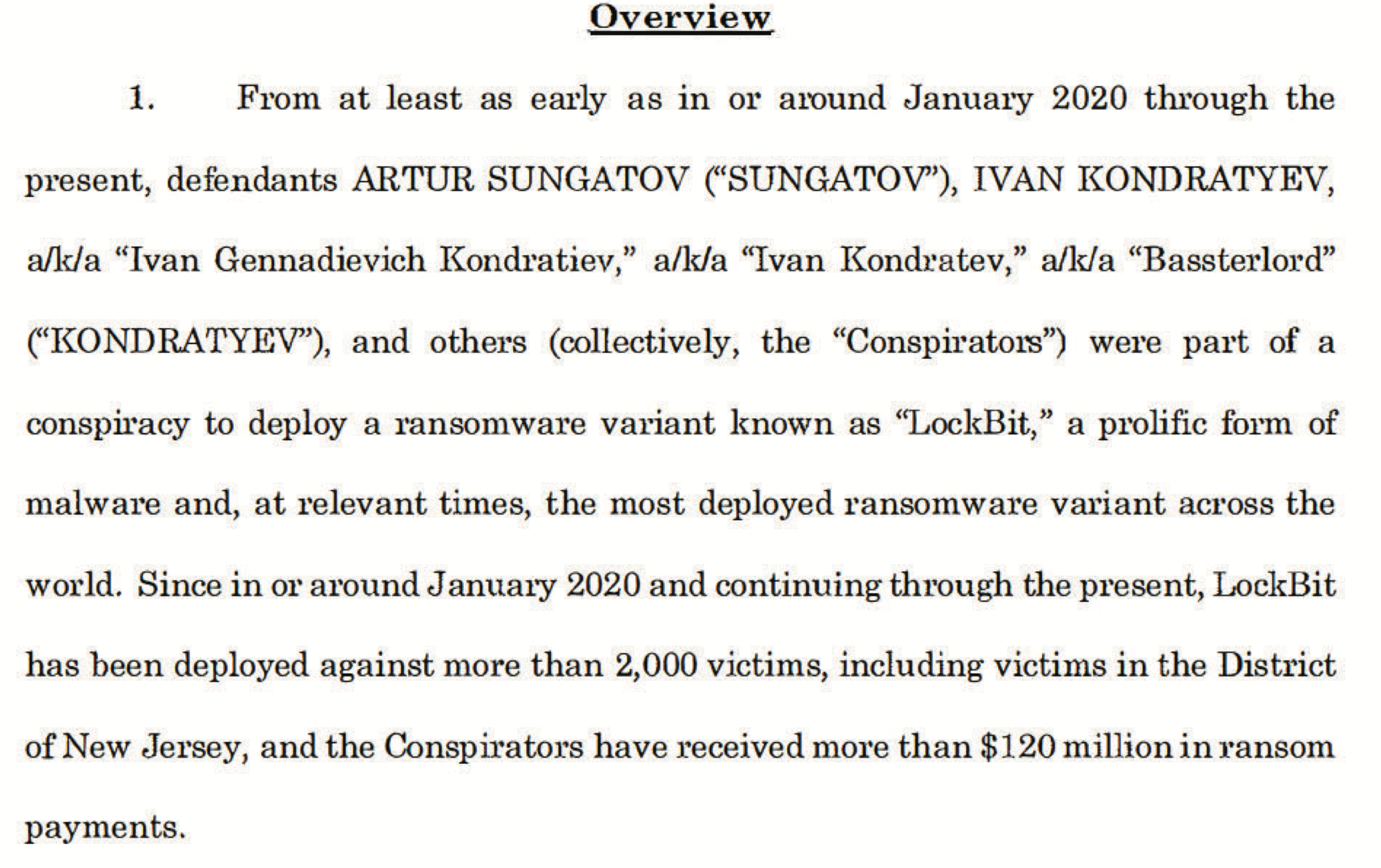
The US government believes LockBit took in about 120 million dollars since 2020. Yes, in less than four years LockBit took in over 30 million dollars a year. That is a lot of money, the market will seek to exploit it.
4. Security cameras that did not understand the privacy part of the assignment.

Users of home security camera provider Wyze learned they can see other peoples’ video feeds thumbnails, and other people can see theirs’—because Wyze designed their systems in a way that when Amazon Web Services (a pretty well known and established, dare I say reliable provider of cloud services) lost power somehow Waze’s cloud configuration stopped segregating peoples’ data, and allowed those thumbnail-links to cross accounts. This leads to customers getting alerts for things happening in other customers homes, and well—being able to snoop into other peoples lives.
There are concepts of fail safe and fail secure in information security, they exist because from time to time human experience tells us things like the power goes out. Under either concept, a networked home security camera should (during a power outage or service drop of some kind) not make its video feed available to, well, kind of anyone. And saying “well it was an AWS outage” when outages are foreseeable and can be planned and more importantly designed against…that doesn’t work.
Let me phrase this another way—Wyze designed a home security camera that will mingle video feed thumbnails during a readily predictable event, and want you to blame it on the event rather than Wyze design choices. But it was only thumbnails, Will! It shouldn't even be thumbnails!
That is a design flaw. A fundamental systems design flaw. That keeps happening.
Oh that AWS outage? AWS did not report one.
## The shift change is a collection of timely stories of interest in the security, privacy, and intelligence worlds. Thanks for reading, and feel free to reach out to will@signaltonoise.fyi for any questions, comments, or thoughts on items you’d like to see highlighted (especially if it’s free, virtual, or networking that could help the community as a whole).