shift change 2024-02-19
Welcome to your shift change report: news (with a pinch of zesty analysis) from the off-going watch to the oncoming on anything interesting in privacy, security, or intelligence.

A shorter shift change today as I look at two attribution stories: one Russian, one American.
1. Cool things you cannot do without attribution—using the Federal Rules of Criminal Procedure to kill a Fancy Bear botnet.
Rule 41 allows criminal investigators to apply for a warrant (based on probable cause) to seize property used in (alleged, based on the phase of the case) digital crimes. Here, the FBI (with cooperation from the infected Ubiquit device owners), analyzed and attributed the malware (a Mirai-based botnet called Moobot) and applied to a federal judge to go beyond analysis and attribution to technically (with technology, not a technicality) neutering the infection.
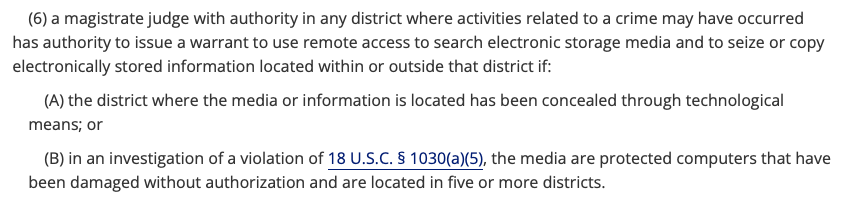
You cannot do this without attribution. Identifying the who, and usually the where, are fundamental to getting results out of the law enforcement agencies of the federal government.
If you want ALPHV to come down, if you want botnets knocked offline, if you want Russians in Russian networks and not US edge routers—you need to do the work to say who is where and doing what. Next time someone tells you attribution is not worth it, ask them worth what? If it is imposing cost and friction on your adversaries and making it harder and harder for them to operate in ways that cost you money, time, and reputation…
Well, I’m for attribution, clearly. For the affidavit (how the investigators got to probable cause for the warrant) and the warrant itself (what the judge actually orders or allows) check out the linked pdf just below the very words you are reading now. The takeaways of the document set are in Paragraph 2 of the affidavit, everything else is detail and specifics.
2. Attribution works on Americans too—here is an American running a DDos-for-hire service.

Targeting a major US public school system is a choice, and not a quality, well-thought out one at that. There are soft targets, and then there are soft targets that can bring to bear non-soft resources, and US institutions are incredibly soft targets but they do not stay that way.
Here’s my takeaway: don’t do this. Do something else with your time and energy—take up knitting or yoga. Enjoy Baldur’s Gate 3. You will get caught if you are in the US and set up a DDoS service and start providing that service against public institutions (I feel crazy just having to type all that out,) and if you are in the US you will enjoy the attention of the court system.
You can do it overseas from outside US jurisdiction, but you may still end up indicted and your travel and banking options may be limited to, well the usual suspects.
## The shift change is a collection of timely stories of interest in the security, privacy, and intelligence worlds. Thanks for reading, and feel free to reach out to will@signaltonoise.fyi for any questions, comments, or thoughts on items you’d like to see highlighted (especially if its free, virtual training or networking events that could help the community as a whole).