shift change 2024-02-15
Welcome to your shift change report: news (with a pinch of zesty analysis) from the off-going watch to the oncoming on anything interesting in privacy, security, or intelligence.

1. Courts (and other basic local government functions) remain soft targets for any type of cyber disruption—I blame attorneys (at least for court system softness).
The year is 2021, and I am a newly licensed attorney sitting for coffee with a more experienced attorney. He asks what my career plans are, what do I want to do? I tell him I want to use my background in network and communication security, with my brand-spanking-new license to practice, to help people and institutions prevent, or disrupt, attacks from the digital domain.
He replied, that is what insurance is for, and told me he didn’t see a business model in helping professional service providers or their infrastructure protect themselves before an attack. Because it would all be handled by insurance.
The revelation comes nearly two and half weeks after the county first acknowledged a “cybersecurity incident” was causing disruptions throughout county systems. Hours before Pitts’ comments, a notorious, multinational cybercrime group claimed responsibility for the hack and posted online what appeared to be internal Fulton County documents, including a police report and a retirement statement.
Cybercriminal groups often publicly list victims in an attempt to pressure them into paying a ransom to recover their data. The leak will only up the stakes for Fulton County to get a handle on a cyberattack that has hobbled services for weeks.
The group that claimed Fulton County as a victim is a prolific group known as LockBit. Their malware was used in ransomware attacks on hundreds of victims the first half of last year alone — more than any other group, according to cybersecurity researchers.
Not only does insurance not solve this, the freaking United States government has not been able to, either.
Fulton County’s ransomware attack comes amid a years-long effort by the US government to limit the damage of ransomware attacks on local governments, hospitals and other critical infrastructure. While there have been notable arrests and law enforcement seizures of millions of dollars’ worth of ransom payments, the ransomware economy continues to thrive.
But, sure, get Jake from Allstate on the line and I'm sure he's got this.

Since the SEC put out new rules requiring timely disclosure of material impacts to business value by cyber threat actors we have seen the industry lose its mind trying to figure out what “material” means (ask your attorney, it is well defined in the law governing fraud going back hundreds and hundreds of years), we’ve seen threat actors try to get ahead of the reporting timeline by reporting their own attack to the SEC to the pressure the victim.
Now, finally, we have a company getting ahead of that game and notifying the SEC, not out of an over-abundance of caution, but out of simple good risk management. If you are having a long, drawn-out discussion of whether something is material, you are treading into the realm of convincing yourself it’s not material. Prudential avoids that headache of that scenario, robs the threat actor a new pressure point, and most importantly to me—acts with some freaking transparency. Bravo, Prudential, bravo.
The potential for weaponizing the new SEC regulations is evident in the case of MeridianLink, which opted to not negotiate with the ransomware group ALPHV (aka BlackCat) after a cyberattack. The gang responded by filing a formal complaint with the SEC, alleging that its recent victim failed to comply with new disclosure regulations.
"The proactive holding statement by Prudential is indicative of the pressure being put on cybercrime victims by cybercriminals under this new incident reporting regime," Mandy says. "It is a sign of a well-rehearsed incident response program."
He adds, "cybercriminals can and will be threatening public disclosure of the incident to extort money from the victims. An early disclosure like this relieves that pressure, but it requires modern data security tools to determine the likely materiality of the incident."
Take 👏 away 👏 your 👏 adversaries' 👏 options 👏, to deny 👏 and 👏 frustrate 👏 their goals 👏 .

It is well past the time where “are threat actors using the full potential of modern technology to accomplish there goals” is a reasonable conversation to have about large language models, OpenAI and Microsoft agree because they are already knocking threat actors of the platform.
Identified groups include Salmon Typhoon (China), Charcoal Typhoon (China), Crimson Sandstorm (Iran), Emerald Sleet (North Korea), and Forest Blizzard (Russia). So not only do we have a variety of new names for non-playable characters or crime syndicates in a Dungeons and Dragons game, we have a full set of Big 4 nation-state cyber threats all in on using superior language technology to enhance their espionage and influence operations.
Expect phishing attacks to improve the appearance of language fluency, but also start tracking if particular LLMs have predictable outputs that can be detected in incoming messages.
Here are the techniques Microsoft and OpenAI have identified and classified to help defenders or intel folks:
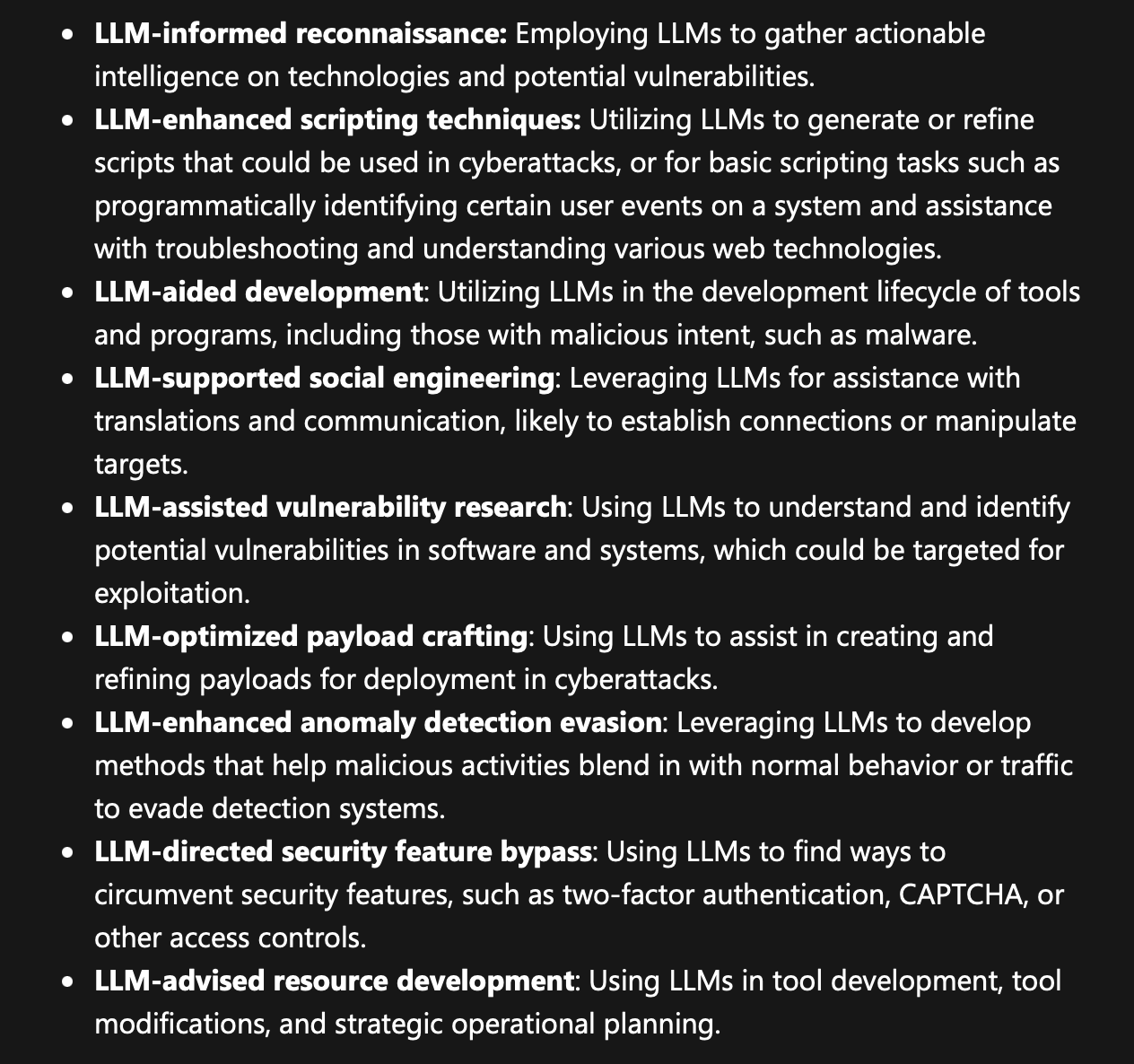
Microsoft mapped the techniques to MITRE ATT&CK and ATLAS, go straight to the source.
## The shift change is a collection of timely stories of interest in the security, privacy, and intelligence worlds. Thanks for reading, and feel free to reach out to will@signaltonoise.fyi for any questions, comments, or thoughts on items you’d like to see highlighted (especially if its free, virtual training or networking events that could help the community as a whole).