shift change 2024-01-31
Welcome to your shift change, reports from the off-going watch to the oncoming on anything interesting in privacy, security, or intelligence.
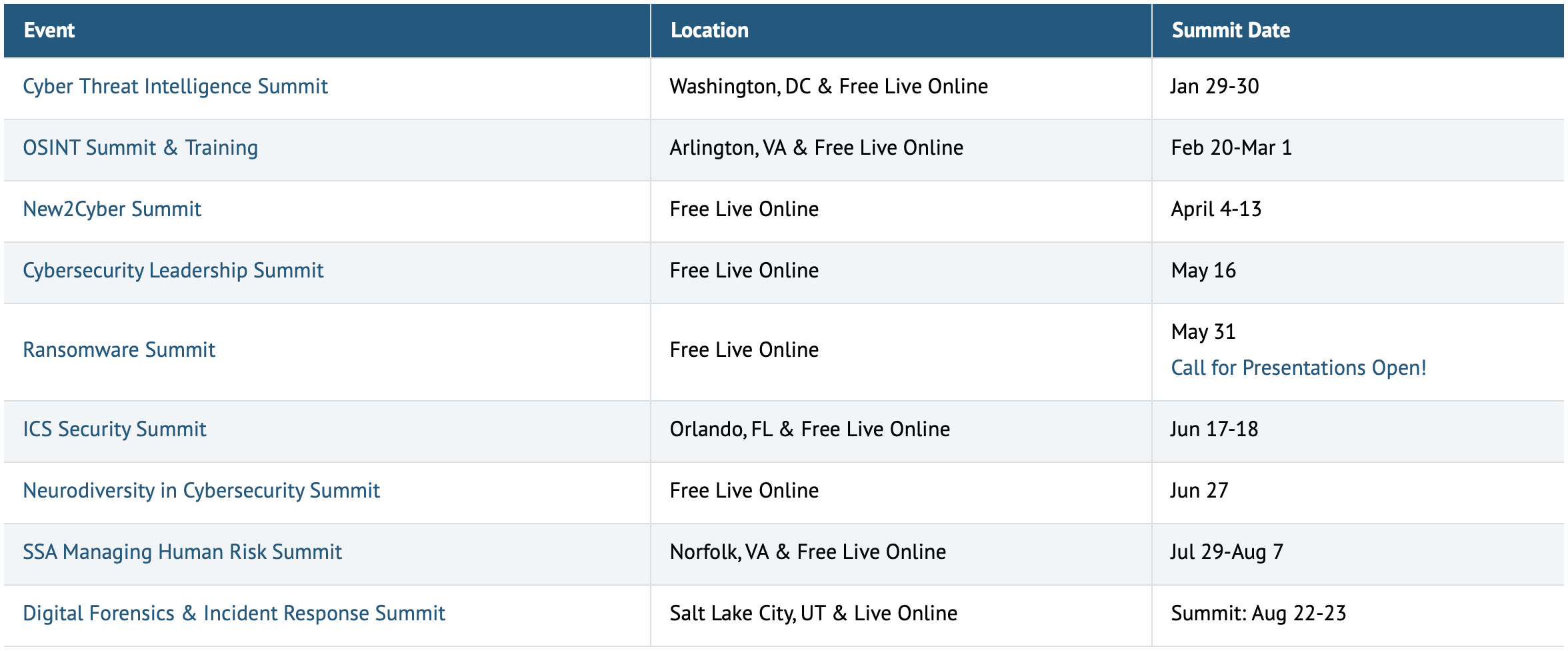
1. SANS 2024 CTI Summit has come and passed; it was a lot of fun and I enjoyed every session along the way—particularly Joe Slowik pushing the community to really thing about what it is trying to communicate when we talk about indicators of compromise, and Grace Chi’s talk on the importance of networking (not just for finding a job!). And I didn’t hear the term “cyber war” until late in day 2—great progress as a community.
But while we wait for the talks to come out on video and for the powerpoint decks to make their way around, I highly recommend checking out the other free virtual talks SANS offers throughout the year, and get into a rhythm of showing up so you see the talks and speakers develop over time. It’s free professional development.
I am already registered for:
SANS OSINT Summit 2024 (February 29-March 1, 2024)
SANS Ransomware Summit 2024 (May 31, 2024), and
SANS DFIR and Summit 2024 (August 22-23, 2024).
2. More privacy features that are not digital: fencing around your home, and plants to support your privacy fencing.

3. “This is a different and novel way we’re seeing abuse that can be pretty hard to detect,” Mandiant researcher Yash Gupta says about activity associated with UNC4990 found while supporting Are Technica and Vimeo investigations.

The full report, direct from Mandiant: here. After listening to Joe Slowik’s talk at the CTI Summit—look at all those host and network-based IOCS, or are they? Having IOCs under Detection Opportunities makes sense—the ultimate value in an IOC is evaluating against your own environment to detect malicious activity, after all.
4. Attribution matters—you cannot try to disrupt Volt Typhoon without first being able to scope the concept of what Volt Typhoon is, and what it wants to and can do:
The big concern is that the threat actor is helping lay the groundwork for capabilities that would let China disrupt capabilities in the Indo-Pacific region that support or service US military operations in the area. "Sources said US officials are concerned the hackers were working to hurt US readiness in case of a Chinese invasion of Taiwan," Reuters said.
Microsoft, one of the first to publicly report on Volt Typhoon last May, has similarly concluded that the threat actor's objective is to develop capabilities that would allow it to disrupt communications infrastructure between the US and the Asian region during a future crisis. The group's victims have included organizations in the communications, transportation, maritime, government, utility, and information technology sectors.
If the US government can identify Volt Typhoon infrastructure, especially where Volt Typhoon may be relying on US company or allied infrastructure, a FRCP Rule 41 motion may get the ball rolling on denying Volt Typhoon the land it wants to live off of.
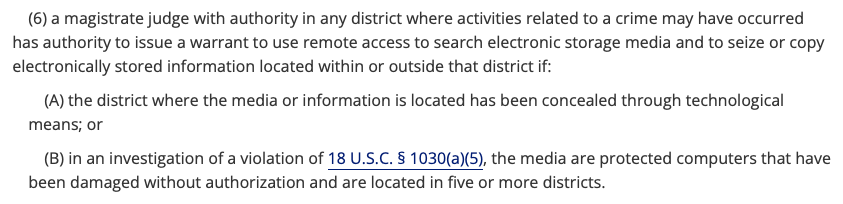
Oh! Just like this:
According to Reuters, the US government has asked several unnamed cloud computing companies, telecommunications firms, and private technology companies for their assistance in tracking and taking down Volt Typhoon activity. Officials from the White House have met with leaders from private sector stakeholder organizations, Reuters said, to discuss plans for disrupting Volt Typhoon activities.
## The shift change is a collection of timely stories of interest in the security, privacy, and intelligence worlds. Thanks for reading, and feel free to reach out to will@signaltonoise.fyi for any questions, comments, or thoughts on items you’d like to see highlighted (especially if its free, virtual training or networking events that could help the community as a whole).